Mobile Edge Computing: The Future of True 5G
Spiceworks
APRIL 17, 2023
Driving the future of 5G with mobile edge computing. The post Mobile Edge Computing: The Future of True 5G appeared first on Spiceworks.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Spiceworks
APRIL 17, 2023
Driving the future of 5G with mobile edge computing. The post Mobile Edge Computing: The Future of True 5G appeared first on Spiceworks.

Spiceworks
JULY 21, 2023
The post Overcoming Zero Trust Challenges with Edge Computing appeared first on Spiceworks. Could edge technology make zero trust security more financially and logistically feasible?

BMT Office Administration
JULY 14, 2023
Mail scams may be making a comeback, but the quickest, easiest, and most efficient way for a scammer or phisher to steal employees’ identities is to hack into your computer network. But ESS portals are risky, too, because they create more points of entry into your computer network for phishers to create havoc.

All Work
AUGUST 8, 2022
It’s not an exaggeration to say that from 1980 to 2010 it was IT networks rather than human networks that drove the design of office space. Image courtesy of MillerKnoll.

Workplace Insight
DECEMBER 11, 2023
Networks are replacing production processes. Tom Cheesewright recently wrote : “organisations are increasingly structured as networks of smaller components” and that the “most extreme example of a networked organisation is one composed entirely of freelancers.

Work Life
MARCH 13, 2025
Computer and information research scientist Median annual salary: $157,160 Estimated job growth (2023 to 2033): 26% Typical educational requirements: Master’s degree in computer science or related field 4.

Insperity
JANUARY 24, 2023
Virtual care allows employees to access the health care system and other health-promoting resources remotely via computers, tablets and smartphones. But, the value of a virtual care option goes beyond a fad and should be considered if you’re actively evaluating how to improve your health care benefits offerings for employees.

Spiceworks
JULY 5, 2023
ARPANET was the first operational computer network that became the foundation of the modern internet. The post What Is ARPANET? Definition, Features, and Importance appeared first on Spiceworks.

Spiceworks
MAY 30, 2023
SCADA uses computers, networks, and user interfaces to remotely monitor and control industrial processes. The post What Is Supervisory Control and Data Acquisition (SCADA)? Definition, Types, and Software appeared first on Spiceworks.

Eat Your Career
JANUARY 29, 2013
While I don’t believe this entirely (to me, it’s both what you know and who you know), I definitely agree that having a strong professional network is a critically important part of creating career success. Unfortunately, a lot of people don’t think about expanding their network until they need something—like a job.

All Work
OCTOBER 18, 2022
Despite this, many corporate leaders are struggling with how to lure workers back to the office by combining mandatory attendance policies with perks like snacks and company-provided lunches, citing collaboration, innovation and networking as the need for in-office days.

All Work
JULY 13, 2023
These impromptu connections allow people to build their networks and professional skills. Plus, coworking spaces may also host networking events, allowing people to further connect. From high-speed internet to state-of-the-art computers to collaborative tools, these spaces are designed with speed and productivity in mind.

All Work
JUNE 19, 2024
Fundamentally it ensures all the systems can communicate and work with each other and with the base building systems and network. Document management systems and cloud computing further support sustainability by reducing the need for paper and enabling more efficient resource management.

Insperity
AUGUST 15, 2019
Establish processes to monitor your network for suspicious behavior. If there is no IT department, consider hiring an IT security firm or consultant to assess the company’s computer network and address security weaknesses to prevent a future data breach. Immediately engage your company’s IT personnel about the breach.
Work Life
OCTOBER 29, 2024
Almost every day, there are news articles about unexpected uses for ChatGPT , from helping doctors empathize with patients to a $3 trillion-dollar market capitalization for Nvidia, which makes graphics processing units (GPUs) used to train deep learning networks. After giving a talk, I am often asked: will I lose my job to AI?

Insperity
JANUARY 24, 2019
Before you can make yourself an indispensable employee, you need to think about daily, routine tasks that could be more efficiently done by computer software. Promote networking. Scheduling meetings. – If you’re tasked with constantly juggling meetings for multiple team members, automation could absorb this responsibility.

All Work
AUGUST 18, 2024
But as employees, too many of us spend long stretches of time indoors breathing in recirculated air and staring at a computer screen with limited movement throughout the day. Employees at RPG Pacifica (left) can raise over-sized window walls to bring fresh air and daylight deep into the office.

Insperity
JUNE 20, 2024
Examples of highly skilled employees Although technical and scientific fields – engineering, computer programming or health care – may come to mind first, highly skilled workers can be found in any industry or profession. They also encompass a diverse range of ages, experience levels and educational achievement.

Insperity
MAY 7, 2020
It can be a risky proposition to allow personal devices to access your company network and resources. If your organization is unable to deploy company assets, your IT team should consider how they will evaluate personal devices before they can connect to your company network and resources. What does this mean?

All Work
MARCH 27, 2023
They proposed that the structure of the living building be formed by enabling native trees to grow over a CNC (computer designed) plywood scaffold. Mycelium is the root network of fungus. Source: Inhabitat Using the past as a source of inspiration The Fab Tree Hab team utilized contemporary technology and drew on old methods.

BMT Office Administration
FEBRUARY 18, 2025
Network security guidelines Specify the rules for accessing the company’s network, including in-office Wi-Fi usage, firewalls, and guest access. If you want employees to use VPNs when accessing the network or handling sensitive data, explain that as well. It also avoids storing them in someone’s notes app.

Insperity
APRIL 26, 2016
When employees use their own devices for work purposes, they’re responsible for keeping your company’s networks and data secured. Be transparent when you’re looking at a phone, tablet or computer screen that others can’t see, and your staff will be encouraged to do the same. Or, you can lead by example, which leads us to the next tip.

Great Place to Work
SEPTEMBER 23, 2024
At Cadence , which hires primarily college graduates with advanced degrees in computer science and technology, a revamped outreach program on campuses created a much bigger talent pool for the company. Roles were changed to target undergraduates and focus on internal training, and a wider range of universities were targeted for recruitment.

Insperity
AUGUST 27, 2014
Take, for example, the military tank mechanic or the computer operator: While their exact experiences may not match your requirements, their foundations in mechanics and technology may put them ahead of other candidates in experience and performance. How to find candidates with military background.

Insperity
NOVEMBER 14, 2019
Although technical and scientific fields – engineering, computer programming or health care – may come to mind first, highly skilled workers can be found in any industry or profession. Request candidate referrals from people in your professional and educational network, including industry peers and fellow alumni.
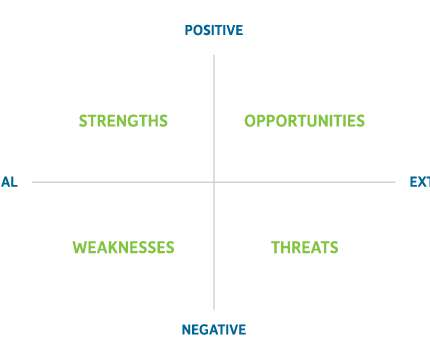
Insperity
JANUARY 14, 2020
You can use any media you prefer, such as: A large piece of paper affixed to a board or easel A dry erase board Projection from your computer onto a blank wall or screen Collaborative platform with shared access, such as a Google document. What are the environmental factors that could cause our business operations or project to suffer?

Insperity
DECEMBER 26, 2019
Witnesses to the rise of computers (“digital immigrants”). All they know is technology (schools often don’t have textbooks, chalkboards or overhead projectors – so this group grew up on computers, smartphones, tablets and other mobile devices, and they’re extremely proficient at using them). Independent and self reliant.

The Receptionist
SEPTEMBER 26, 2022
Protect Your Network Cybercrime is predicted to cost $8 trillion USD worldwide in 2023. Which is why it’s so important that every part of your network is protected. Be sure to set up two separate networks: one for your visitors and one for your clients who need to access their work from a secured connection.

Insperity
MARCH 2, 2017
Opportunities to network with potential clients, vendors and new employees. Are electrical cords from computers strung across walkways? Benefits of co-working spaces for larger businesses include: Provides remote employees with a more professional, less isolated environment than working from a home office. What is the noise level?

Insperity
JULY 30, 2020
Portraying an undesirable image on social media: This is especially important on employment related sites such as LinkedIn and Glassdoor, but it’s also becoming a more prominent issue on all social networks including Facebook, Instagram and Twitter. Ask your IT team to block access on office computers to certain categories of websites.

Insperity
MAY 19, 2022
After all, they don’t remember a world without computers, the internet, email, social media, cell phones and a host of other conveniences that are now commonplace. Many of them have little to no experience in a traditional 9-to-5, on-site work setting. They tend to be very comfortable with technology , especially digital communication.

All Work
SEPTEMBER 3, 2024
Myth: Data Centers Are Being Replaced by the Cloud Reality: The Cloud Relies on Data Centers One of the most persistent myths is that the rise of cloud computing is rendering traditional data centers obsolete. Companies like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud operate vast networks of data centers around the world.

The Receptionist
JULY 5, 2022
Denial-of-Service (DOS) Attack In this method of attack, a criminal floods your server, system, and/or network with so much traffic that the system overloads and cannot handle or process the number of requests. This creates a vulnerability that allows the criminal to enter your network.

Insperity
JUNE 6, 2023
After all, they don’t remember a world without computers, the internet, email, social media, cell phones and a host of other conveniences that are now commonplace. Many of them have little to no experience in a traditional 9-to-5, on-site work setting. They tend to be very comfortable with technology , especially digital communication.

Fellow
DECEMBER 12, 2023
The role and responsibilities of a software engineer Why all software engineers should have goals 22 goals for software engineers The role and responsibilities of a software engineer Software engineers design and develop everything from business applications to computer games. 13 Expand professional networks Your network is your net worth.

Insperity
JANUARY 15, 2012
When you are backing up data, remember to include financial data, key human resources files, custom software, contracts or other legal documents, databases, insurance files and computer system backups, says Matthew Putvinski, director of Wolf and Company’s Information Technology Assurance Services group. Secure off-site. Vet vendors.

C-Suite Assistants
JANUARY 10, 2025
Knowledge workers such as executive assistants (EAs), who spend much time on computer-related tasks can benefit greatly from this arrangement, as can employers. Our extensive professional network includes tech-savvy assistants with deep experience working remotely and in hybrid situations. In many instances, work spaces can be shared.

Ask a Manager
APRIL 9, 2023
Are there any limits on employee computer monitoring? I have reason to believe my employer is planning to install desktop monitoring software on at least some computers within our organization. Legally, employers can monitor anything done on their devices or their networks.

Spiceworks
APRIL 17, 2024
A fully qualified domain name (FQDN) is the complete name for a specific computer or network resource, including both the hostname and the domain name. Learn how FQDN works and its importance with detailed examples. The post What Is a Fully Qualified Domain Name (FQDN)?

Vantage Circle
AUGUST 14, 2020
At the same time, many workers offer companies direct benefits by improved social media enabled contact, advertisement, and networking. Research has revealed that 82 percent of workers agree that social networking will strengthen working relationships. Digital natives also use social networking as a means of development opportunities.

Success
FEBRUARY 21, 2023
It felt alien to Arocho, who was accustomed to real-life networking on the road and meeting people in person. “It If I was in front of the computer, it felt like I wasn’t doing anything. I realized it’s OK to be in front of the computer for an hour.” It was a regimen I had to get used to,” he says. “If

Success
FEBRUARY 24, 2022
Farah Hawa , an application security engineer and bug bounty hunter, points out that “free Wi-Fi could be set up in a public place by malicious players, or they may be on the same public network as you. Often, we forget that others around us can see much of what we’re doing on our computers. Safeguard your data even at home.

Success
APRIL 24, 2022
Bitcoin runs over a network of computers that belong to many people, spread out across the globe, who are collectively charged with maintaining and validating its ledger of accounts. Thousands of individual computer systems must all validate each transaction that occurs on the bitcoin blockchain ledger.

The Receptionist
MARCH 6, 2023
Hackers can access your visitors’ private information by exploiting vulnerabilities in your network and using that information to steal their identity. Here’s how to protect your chiropractic office and your visitors from cyber threats: Use strong passwords for your work computers and software programs. Use a secure wireless network.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content